December 3rd 2016 marks 10 years since sks-keyservers.net was first announced on the sks-devel mailing list. The time really has passed by too quickly, driven by a community that is a pleasure to cooperate with.
Sadly there is still a long way to go for OpenPGP to be used mainstream, but in this blog post I'll try to reminisce on a few things that have happened since Bjørn Buerger commented about *.keyserver.penguin.de being down, which lead to the need for a DNS Round Robin alternative. Having a common DNS Round Robin to use is practical for a number of reasons, mainly; (i) Its easier to communicate to users (ii) It distributes the load across multiple keyservers (iii) Non synchronizing/responding keyservers can be removed without users needing to reconfigure the systems.
After the announcement of the new service, Enigmail, the Thunderbird OpenPGP plugin, was quick to change the default preferences to point to hkp://pool.sks-keyservers.net already in December 2006, less than a week after the new service was officially announced.
The GnuPG Project started its usage of the pools when keys.gnupg.net was changed to be a CNAME to the pool in May 2012. Since then the cooperation has evolved, and in particular in the "Modern" 2.1 branch it has been completed. Since 2.1.11 the public key for the Certificate Authority used for the HKPS pool has been used by default if a user specify the use of hkps://hkps.pool.sks-keyservers.net, i.e without needing to specify the hkp-cacert, and with the release of 2.1.16 it is now the default keyserver that is used if a user has no overriding configuration. Earlier versions produced an error message of no keyserver at all in this scenario.
Some slides from my presentation of the first OpenPGP conference, in Cologne 2016, are available describing the current state of operations. And if you want to learn a bit of Norwegian you can watch the recording of the 2014 presentation, or at least read the slides that happen to be in English.
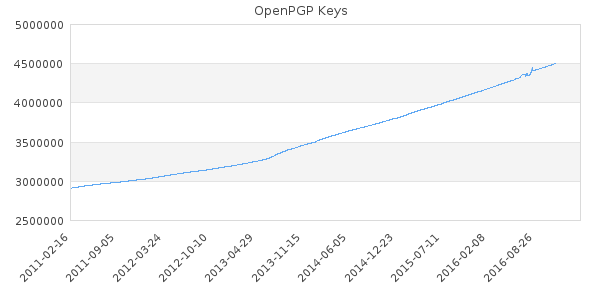
Although the growth in number of public keyblocks has been increasing as demonstrated in Figure 1, it is still a low reach with 4.5 million entries. How about we use the next 10 years to make sure it becomes mainstream?