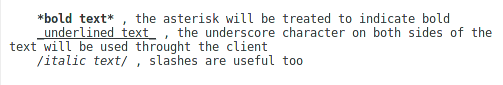
On June 27 Microsoft announced they would stop sending security bulletins by email. The announcement stated:
As of July 1, 2014, due to changing governmental policies concerning
the issuance of automated electronic messaging, Microsoft is
suspending the use of email notifications that announce the
following:
* Security bulletin advance notifications
* Security bulletin summaries
* New security advisories and bulletins
* Major and minor revisions to security advisories and bulletins
In lieu of email notifications, you can subscribe to one or more of
the RSS feeds described on the Security TechCenter website.
This change is speculated to be related to a Canadian anti-spam regulation, although the normal course of action would normally be receiving explicit approval for sending these announcements. Some questions have also been asked about the timing of the announcement, as the regulation was known well in advance. Whatever the reason for suspending these services, on July 3rd, Microsoft reversed its course with the following message:
On June 27, 2014, we notified customers that we were suspending
Microsoft security notifications by email due to changing
Governmental policies concerning the issuance of automated
electronic messaging. We have reviewed our processes and are
resuming security notifications by email commencing with the
release of this monthly Advanced Notification Service (ANS) mailing.
Now, a prudent reader might ask why receiving emails constitute a security relevant matter, after all they offer to keep sending announcements through an RSS feed. That brings us to the more interesting matter. Microsoft, rightly so, use OpenPGP digital signatures for the notification emails to make it possible to verify the authenticity of the sender and verify that the message has not been altered in transit. The OpenPGP signed email communication channel is the only available option provided by Microsoft with these capabilities and in order to grab focus on this property, they include the following in their own bulletins:
The Microsoft Security Response Center (MSRC) uses PGP to digitally
sign all security notifications. However, PGP is not required for
reading security notifications, reading security bulletins, or
installing security updates. You can obtain the MSRC public PGP key
at
<https://technet.microsoft.com/security/dn753714>.
So far so good; Microsoft is using OpenPGP and they are announcing their public key. Other people should do this as well.
Sadly it goes downhill from here: Despite Microsoft announcing a HTTPS website for the acquiring the public key used for these announcements, upon attempting to contact this URL, a HTTP 302 redirect is used with the following Location: http://technet.microsoft.com/security/dn753714 , i.e .without any protection from TLS at all. This opens up possibilities of various man-in-the-middle attacks, hence removing the possibility validating the provided public key.
Of course, this shouldn't normally be an issue, as OpenPGP keys rely on object security which is self-contained together with the key material itself - which is why keys are normally distributed through various keyserver networks. Before using any OpenPGP key the key will have to be validated by the participant, either directly with the owner of the key or through the Web of Trust (WoT).
If we are to trust that we have not been MiTMed just now, Microsoft is linking to public key information presented as a 4096 bit RSA key for Certificate and Signing use with a 4096 bit subkey for Encryption.
And here is the kicker; The key was created on 2014-06-03, i.e. it is a relatively new key, and it does not contain any certifications from any Microsoft employee or signature from earlier keys used for Microsoft Security Advisories as you would normally expect.
To add insult to injury, despite the emails containing references to the aforementioned website and key, the following Microsoft announcements on July 10 and 11 were actually signed by the key 0xF0B7406D which is not referenced as a key used for current Microsoft announcements. This key actually does contain a small number of signatures from external users, but as with 0xA92965F2 none from any Microsoft employee. As to whether the key is authentic your guess is still as good as mine.
So why is it so important that the key used for security announcements is signed by individual Microsoft employees, and in particular the members of the security team?
These employees are the only individuals that can reasonably make an assurance about the use of a team key. Additionally, as proper key validation procedures require ID-checks and a personal assertion about the key ownership, for others to get a trust path to the key in question, these members of the team will need to have their own keys verified by other participants in- and outside of the IT industry.
Users that wants Microsoft to try to get its act together when it comes to communication security (to allow a broader scope is probably utopia) should send messages to them through channels such as Twitter (@msftsecresponse). My own posts have not been answered so far.